2degrees stories - Page 8

Security the biggest loser during the World Cup...
Tue, 15th Jul 2014
#
malware
#
phishing
#
email security
The 2014 World Cup hailed as most connected yet, but it was also a playground for cybercriminals, exposing fans to unprecedented online threats.

2degrees narrows 2013 loss
Tue, 24th Jun 2014
#
uc
#
2degrees
#
vodafone
2degrees Mobile reduces 2013 losses by 20%, boasting positive operating earnings and a revenue surge amid ongoing investments.

Check Point: Dangerous phishing attacks in detail...
Fri, 13th Dec 2013
#
malware
#
phishing
#
martech
Phishing attacks and their more recent variations such as spear-phishing and whaling are by now well-known parts of the threat landscape.

Apple-related phishing sites hit ANZ hard
Fri, 15th Nov 2013
#
phishing
#
email security
#
cybersecurity
ANZ rated the third highest region for hosting Apple targeted phishing sites, accounting for 10.7% of the phishing sites blocked globally in Q3 2013.

Vodafone NZ stops the rot, adds 19,000 this qtr
Tue, 23rd Jul 2013
#
uc
#
customers
#
telstraclear
Telco reports customer increase across New Zealand, bucking the previous trend spanning nine consecutive quarters.

NZ mobile data demand doubles
Tue, 30th Apr 2013
#
smartphones
#
uc
#
chorus
New Zealand's mobile data usage has doubled for the second consecutive year, driven by increased smartphone activity, says the Commerce Commission's report.

Spear-phishing: Don’t be the ‘Catch of the Day’
Wed, 26th Dec 2012
#
phishing
#
email security
#
cybersecurity
Phishing emails are designed to look like they come from a trusted source and extort personal information, which gets used in a criminal or fraudulent way.

2degrees ready for mobile data battle
Thu, 12th Apr 2012
#
uc
#
2degrees
#
vodafone
2degrees turbocharges mobile broadband, adding 8 more cities to its network. Aiming to dominate in a tight race with $400M investment.

2degrees customer numbers climbing
Thu, 9th Feb 2012
#
uc
#
2degrees
#
vodafone
2degrees sees customer numbers soar to 875,656, marking a nearly 50% jump with the introduction of business services.

Kiwibank scam warning
Mon, 9th Jan 2012
#
phishing
#
email security
#
kiwibank
Kiwibank warns of phishing scams, urging customers to ignore links in fake emails mimicking the bank's communication for data access.

Tough tech decisions: 2degrees, Telecom, or Vodafone?
Sun, 1st Jan 2012
#
uc
#
personal computing devices
#
2degrees
NetGuide pits 2degrees, Vodafone, and Telecom against each other in a battle for the best mobile carrier, aiming to help consumers decide.

Vodafone claims 2degrees has harmed competition
Thu, 24th Nov 2011
#
uc
#
2degrees
#
vodafone
Why the company is taking the credit for mobile price cuts and saying competition has slowed since 2degrees launched in 2009.
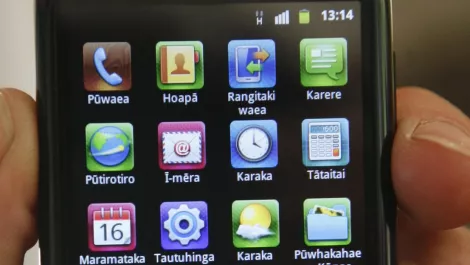
World’s first Te Reo Maori smartphone
Wed, 2nd Nov 2011
#
uc
#
2degrees
#
vodafone
The IDEOS X3 smartphone features menus in Te Reo, and will be available at 2degrees retail stores before Christmas.

200,000 number 'ports' for 2degrees
Wed, 27th Jul 2011
#
uc
#
2degrees
#
vodafone
200,000 New Zealanders have ‘ported’ their number to 2degrees since its launch two years ago, the company says.

Vodafone customer base dips
Mon, 25th Jul 2011
#
uc
#
2degrees
#
vodafone
Vodafone NZ sees a sharp decline of 26,000 customers as market fresh-face 2degrees makes its mark, suggesting stiff competition ahead.

Spammers reducing reliance on Botnets
Thu, 14th Jul 2011
#
malware
#
phishing
#
email security
Report reveals spam at 3-year low as spammers swap botnets for malware and phishing, outsmarting traditional IP blocks.

2Degrees records loss
Mon, 27th Jun 2011
#
uc
#
2degrees
#
vodafone
2Degrees struggles with a £76.8m loss in its fight against Telecom and Vodafone giants, despite a revenue of £107.6m.

Google pushes web safety after inbox hacks
Fri, 3rd Jun 2011
#
phishing
#
email security
#
google
Internet giant pushes safety message after successful phishing attacks on military, government and political Gmail users.

2degrees worried about rural duopoly
Fri, 12th Nov 2010
#
uc
#
broadband
#
2degrees
Rural customers don't deserve a high speed version of the mobile duopoly New Zealanders have lived with for so long, says Chief Executive Eric Hertz.

Can 2degrees and XT top Vodafone’s gain?
Tue, 9th Feb 2010
#
uc
#
2degrees
#
vodafone
2degrees will release its customer numbers on Friday – two and half hours after Telecom reveals the number of subscribers on its XT Network.